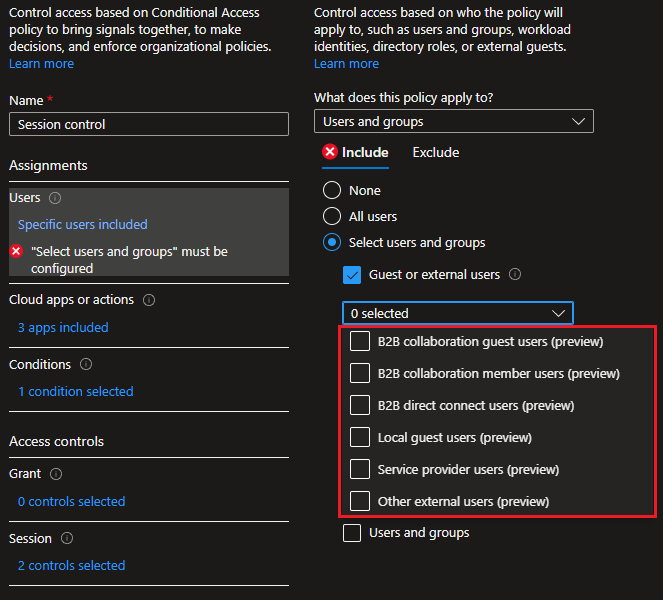
As part of a new preview functionality, Microsoft is introducing an expanded set of controls for Conditional access policies, revolving around granularly including/excluding specific guest users. You will find the new controls as part of the Users and groups > Select users and groups > Guest or external users selection. Therein, you can choose from six types of Guest or external users categories, as follows:
- B2B collaboration guest users – the “standard” type of Guest user. The userType value is Guest, and permissions are inherited from the default Guest user role.
- B2B collaboration member users – similar to the above, but this group includes objects for which the userType value has been converted to Member. Thus they have an expanded set of permissions within the directory.
- Local guest users – represents users created/managed within your own Azure AD tenant, but with userType value set to Guest. The difference with the first scenario is the “source of authority” – in this case your local Azure AD instance.
- B2B direct connect users – currently only represented by Teams shared channel members, those are external users leveraging the B2B direct connect model.
- Service provider users – a special flavor of B2B direct connect, tailored to partners/service providers. Configured by toggling the isServiceProvider flag of a cross-tenant access policy object.
- Other external users – a blanket category, including all other objects that don’t fall into any of the above categories.
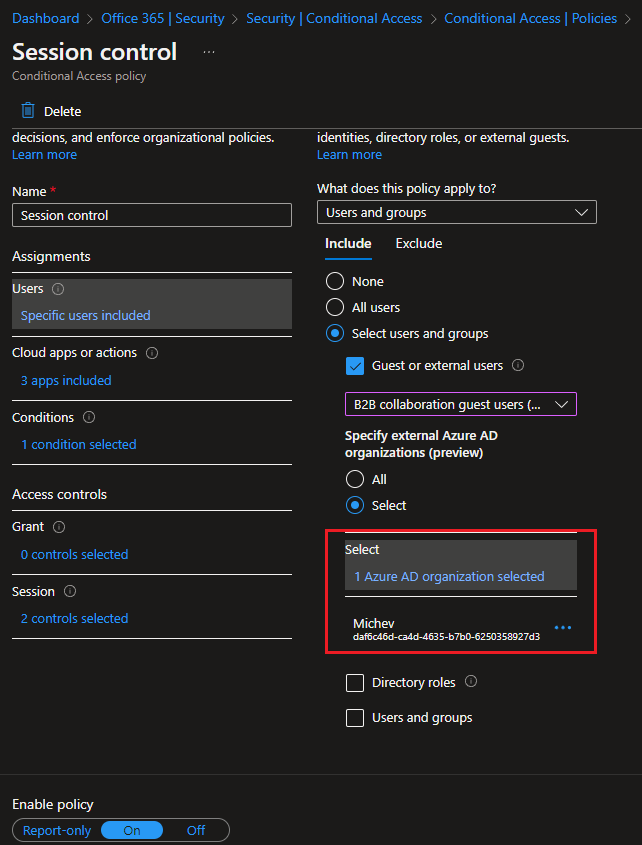
 After selecting one or more of the above categories, you can then select whether to further scope down the control by restricting it to specific Azure AD tenant(s), or choose All tenants. You can specify either the tenant GUID or one of its domains, including the default onmicrosoft.com one or any custom-verified domains. The same controls are also available for the Exclude scenario, giving you a lot of flexibility.
After selecting one or more of the above categories, you can then select whether to further scope down the control by restricting it to specific Azure AD tenant(s), or choose All tenants. You can specify either the tenant GUID or one of its domains, including the default onmicrosoft.com one or any custom-verified domains. The same controls are also available for the Exclude scenario, giving you a lot of flexibility.
 Apart from the UI controls, the set of Graph API endpoints has also been updated to cater to the new functionality, albeit only available under /beta for the time being. We have the includeGuestsOrExternalUsers and excludeGuestsOrExternalUsers properties added to the main CA resource type, both of which are representing a conditionalAccessGuestsOrExternalUsers object. Within said object, the guestOrExternalUserTypes property represents the selection of the six categories as detailed in the list above. The corresponding values to use with the Graph API are as follows: b2bCollaborationGuest, b2bCollaborationMember, internalGuest, b2bDirectConnectUser, serviceProvider and OtherExternalUser.
Apart from the UI controls, the set of Graph API endpoints has also been updated to cater to the new functionality, albeit only available under /beta for the time being. We have the includeGuestsOrExternalUsers and excludeGuestsOrExternalUsers properties added to the main CA resource type, both of which are representing a conditionalAccessGuestsOrExternalUsers object. Within said object, the guestOrExternalUserTypes property represents the selection of the six categories as detailed in the list above. The corresponding values to use with the Graph API are as follows: b2bCollaborationGuest, b2bCollaborationMember, internalGuest, b2bDirectConnectUser, serviceProvider and OtherExternalUser.
The tenant controls on the other hand are represented via the externalTenants property, of the conditionalAccessExternalTenants resource type. Within it, the membershipKind property designates the type of selection made, with possible values of all (to include all Azure AD tenants) or enumerated (specific Azure AD tenants). The latter requires yet another property to be configured, namely the members string collection of conditionalAccessEnumeratedExternalTenants type. Here’s how an example configuration would look like:
"includeGuestsOrExternalUsers": {
"guestOrExternalUserTypes": "b2bCollaborationGuest",
"externalTenants": {
"@odata.type": "#microsoft.graph.conditionalAccessEnumeratedExternalTenants",
"membershipKind": "enumerated",
"members": [
"daf6c46d-ca4d-4635-b7b0-6250358927d3"
]
}
}
Refer to the official documentation for more details. Also do note that once a policy has been updated to use the new controls, you will only find it under the /beta endpoint – don’t panic if no matching object is returned under /v1.0 🙂
im trying to set this guestOrExternalUserTypes via powershell and having no luck finding any examples of this being done or possible,
I have added “guestsorexternalusers” to the excluded users and this does enable the exception for all the guest types, but i want to be more specific if possible
Any hints appreciated
Not entirely sure what you mean by that. The supported user types are listed above, guestOrExternalUserTypes is the property that contains the corresponding values. If you want to add multiple types, separate them with comma:
“guestOrExternalUserTypes”: “internalGuest,b2bCollaborationGuest”
Nice – do you know if partners who have delegated admin via DAP/GDAP are covered under “service providers”? I would assume so, but you mention this tickbox uses a special kind of B2B direct connect which I’m not sure means DAP/GDAP? Cheers 🙂